Incident Response Flow Chart
Incident Response Flow Chart - Web these steps occur as a cyber security incident response flow chart, and the steps involved are: This factsheet provides an overview of an incident response plan and how it should be implemented before, during, and after a cybersecurity incident. Assign, escalate, or document incident management procedures. It’s approved by company management, which means you won’t have to. Web incident response refers to the systematic approach taken to address and handle the consequences of a security breach or attack, aiming to minimize harm and restore regular operations promptly. At atlassian, we define an incident as an event that causes disruption to or a reduction in the quality of a service which requires an emergency response. Web this incident management high level process flow template by pink elephant can help you: Web an incident flow chart is a simple term given to the incident management steps undertaken to deal with a situation of crisis. 2 why include an incident response plan flow chart in your incident response plan? A list of tasks for the steps in the flow chart. Web the nist incident response lifecycle breaks incident response down into four main phases: Web the incident response tool and flowchart guides administrators through all the steps of incident management: Focus on rapidly restoring service to users. Web 1.1 the process contains the following several steps: Web incident management is the process used by development and it operations teams to. When a service fails to fulfill the expected performance, it is mandatory to take action and restore the service to its normal state. Below are steps of each framework: This factsheet provides an overview of an incident response plan and how it should be implemented before, during, and after a cybersecurity incident. Web 1.1 the process contains the following several. Learn the six distinct phases of the incident management lifecycle and best practices for implementing them. Web incident management is the process used by development and it operations teams to respond to an unplanned event or service interruption and restore the service to its operational state. Discover tailored strategies for small businesses and gain insights from real incident response plan. Web an incident flow chart is a simple term given to the incident management steps undertaken to deal with a situation of crisis. Web these steps occur as a cyber security incident response flow chart, and the steps involved are: At atlassian, we define an incident as an event that causes disruption to or a reduction in the quality of. What is incident response planning? Usually, a fundamental strategy in reports and complaints emerges concerning a provider’s benefit. Some incidents can be resolved with a simple checklist, but many require decisions and include branching paths. Gain a deep understanding of incident response and its role within a comprehensive cybersecurity strategy. Explore the four phases and five essential steps for a. What is an incident response plan? 2 why include an incident response plan flow chart in your incident response plan? At atlassian, we define an incident as an event that causes disruption to or a reduction in the quality of a service which requires an emergency response. Incident response planning is the a process of identifying and prioritizing possible threats. An incident flowchart relates to a diagram of steps on how to oversee an occurrence. Web sometimes called an incident management plan or emergency management plan, an incident response plan provides clear guidelines for responding to several potential scenarios, including data breaches, dos or ddos attacks, firewall breaches, malware outbreaks, insider threats, data loss and other security breaches. It’s approved. 2 why include an incident response plan flow chart in your incident response plan? An incident response plan is a document that outlines an organization’s procedures, steps, and responsibilities of its incident response program. Web 1.1 the process contains the following several steps: This factsheet provides an overview of an incident response plan and how it should be implemented before,. Web incident management process flow | lucidchart. Usually, a fundamental strategy in reports and complaints emerges concerning a provider’s benefit. It’s approved by company management, which means you won’t have to. Focus on rapidly restoring service to users. Web the nist incident response lifecycle breaks incident response down into four main phases: Web this incident response guide will help you to: Learn the six distinct phases of the incident management lifecycle and best practices for implementing them. This factsheet provides an overview of an incident response plan and how it should be implemented before, during, and after a cybersecurity incident. What is incident response planning? Web these steps occur as a cyber. Cybersecurity best practices, election security. Web the incident response tool and flowchart guides administrators through all the steps of incident management: Web incident response refers to the systematic approach taken to address and handle the consequences of a security breach or attack, aiming to minimize harm and restore regular operations promptly. Some incidents can be resolved with a simple checklist, but many require decisions and include branching paths. Usually, a fundamental strategy in reports and complaints emerges concerning a provider’s benefit. This factsheet provides an overview of an incident response plan and how it should be implemented before, during, and after a cybersecurity incident. Web this incident response guide will help you to: Web how to create an incident flow chart? Web the nist incident response lifecycle breaks incident response down into four main phases: Web incident management is the process used by development and it operations teams to respond to an unplanned event or service interruption and restore the service to its operational state. When a service fails to fulfill the expected performance, it is mandatory to take action and restore the service to its normal state. Web sometimes called an incident management plan or emergency management plan, an incident response plan provides clear guidelines for responding to several potential scenarios, including data breaches, dos or ddos attacks, firewall breaches, malware outbreaks, insider threats, data loss and other security breaches. It’s approved by company management, which means you won’t have to. Learn the six distinct phases of the incident management lifecycle and best practices for implementing them. It appears how the incident handling works towards its determination. Also see microsoft incident response ransomware approach and best practices.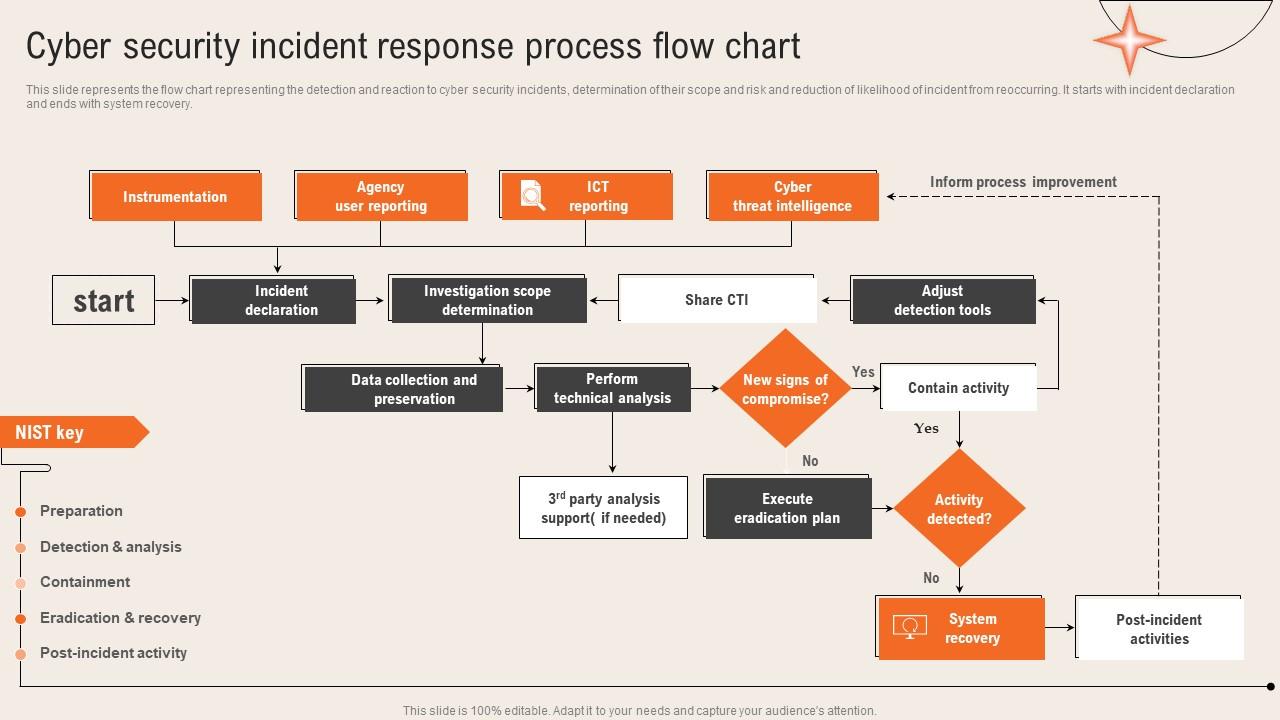
Cyber Security Incident Response Process Flow Chart Deploying Computer

Incident Response Flow Chart Template

How to Create an Incident Response Plan The CPA Journal

Incident Response Flowchart Ferpa Sherpa Flow Chart N vrogue.co
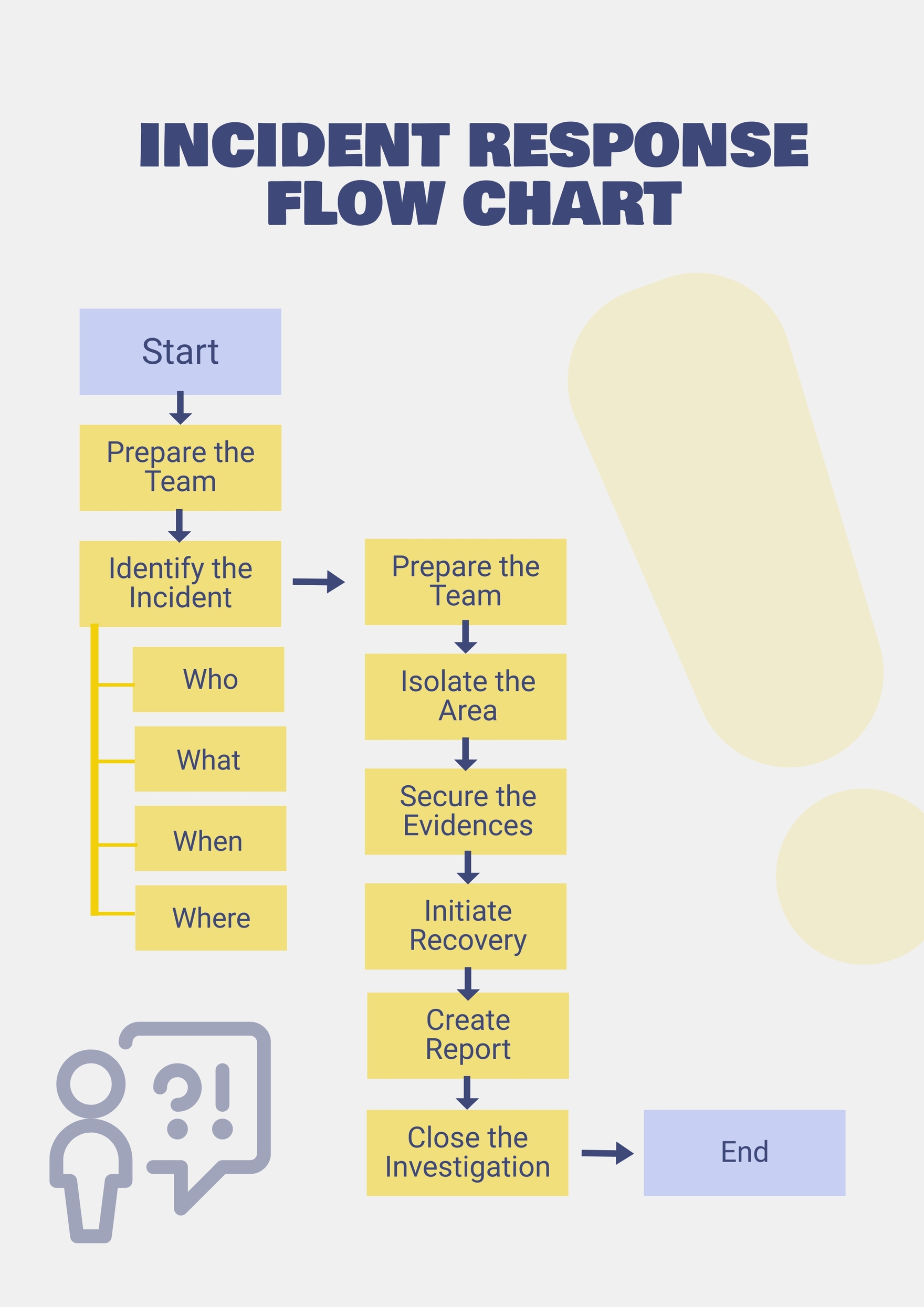
Incident Response Plan Flow Chart in Illustrator, PDF Download
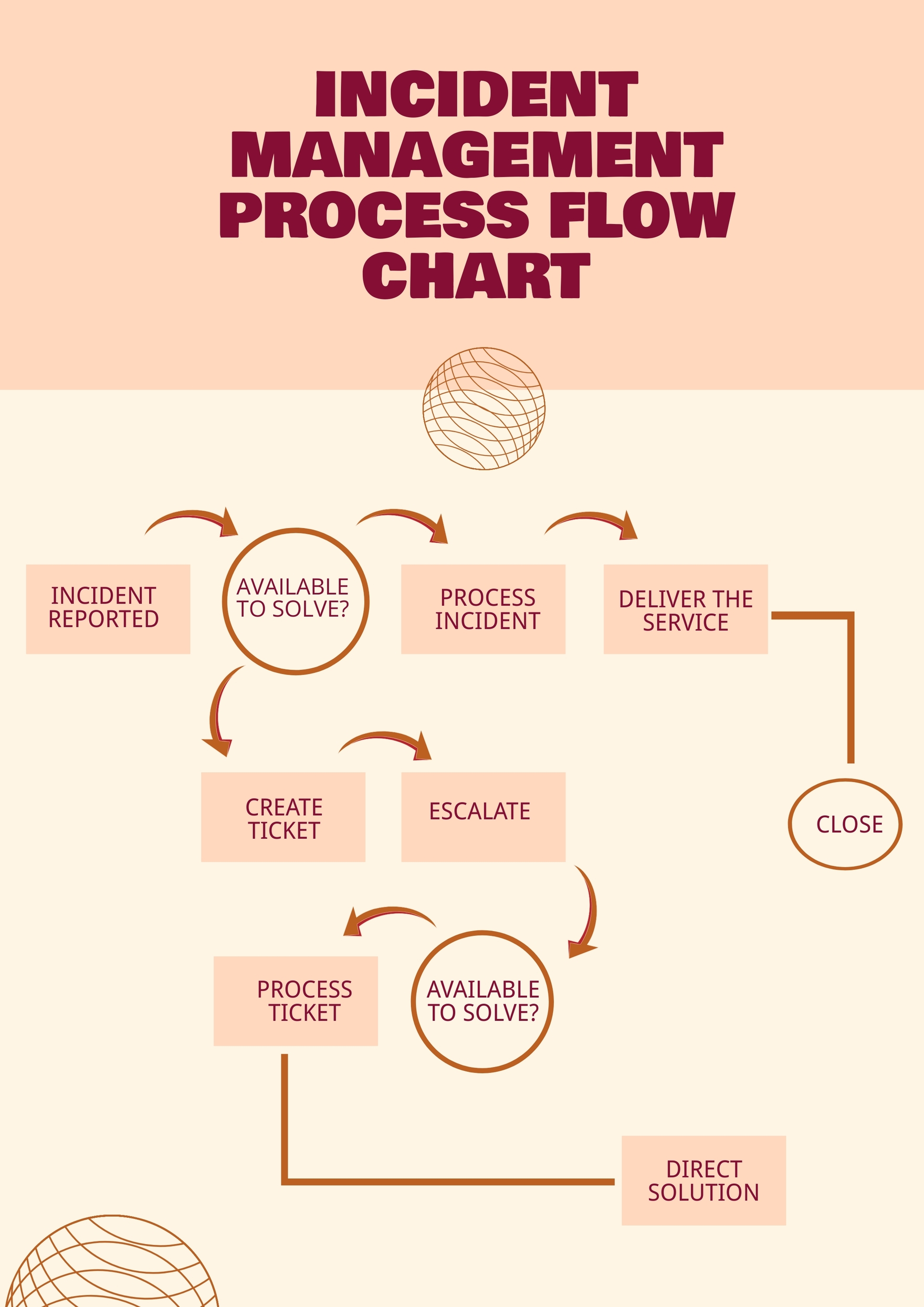
Incident Management Process Flow Chart in Illustrator, PDF Download
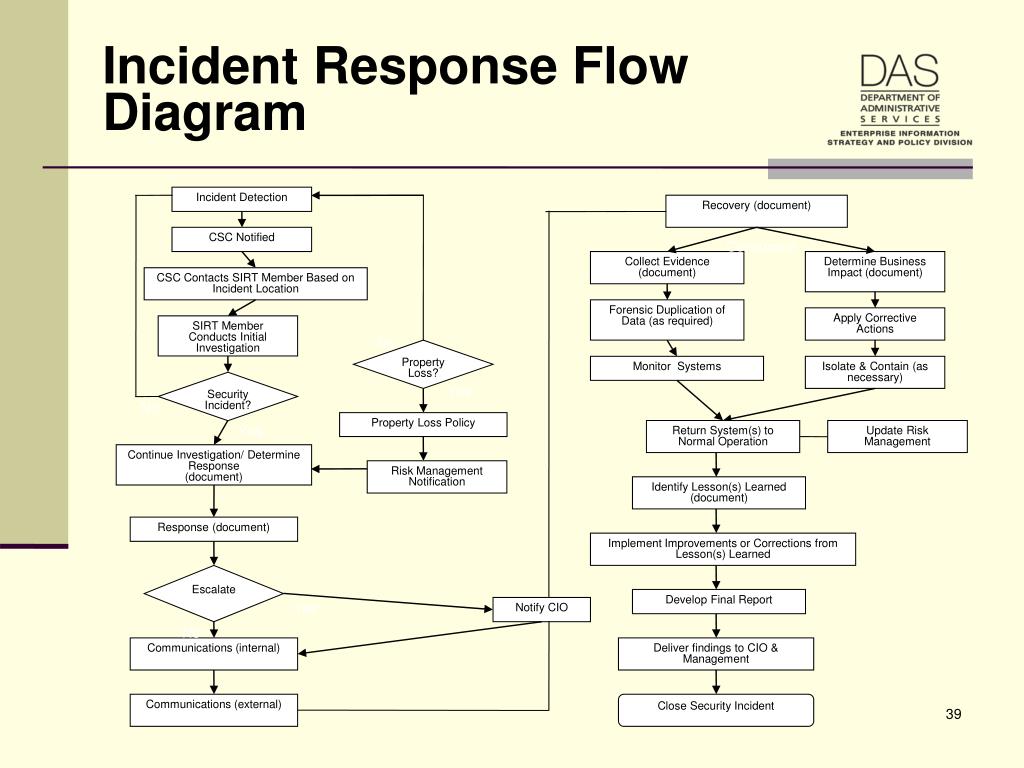
Incident Response Flow Chart Template

Incident Response Test Flow Chart
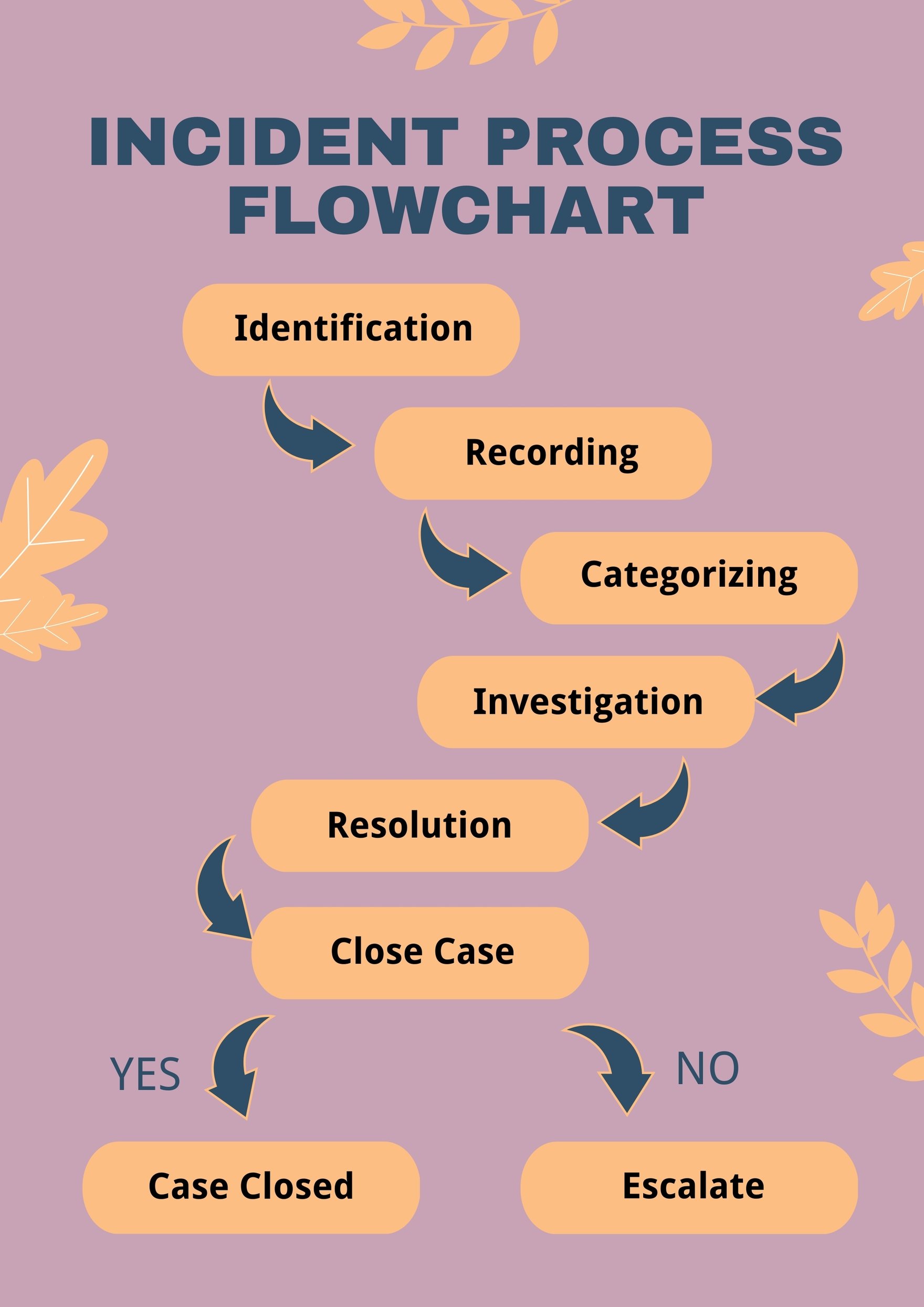
FREE Incident Flow Chart Template Download in PDF, Illustrator
![]()
Understanding the 6 Elements of the Incident Response (IR) Process
Web Incident Management Process Flow | Lucidchart.
Web Diagrams For Incident Response Plans.
Assign, Escalate, Or Document Incident Management Procedures.
What Is An Incident Response Plan?
Related Post: